Privacy-Enhancing Computation

Privacy-Enhancing Computation
Data, with our any doubt, is the most valuable business asset in the current age. And since its value keeps growing, maintaining this asset's safety becomes the highest priority.
As cyberattacks and elaborate techniques used to access data are on the rise, the privacy-enhancing computation (PEC) and technologies (PET) have become a central security measure for organizations.
The technology itself has been around for decades, but only recently it has started being amplified in applications. In this article we would like to discuss modern privacy enhancing computation, its importance and some of the main features.
What is Privacy-Enhancing Computation?
In its very essence, privacy-enhancing computation aims at using a group of various technologies to heighten the level of private data protection. This group of technologies augments privacy protection and provides immunity against violations and hacker attacks.
According to the research made by Gartner, PEC includes three forms of technologies to protect sensitive data:
-
providing a trusted environment where data can be processed securely;
-
processing and analytics through privacy-aware machine learning;
-
technology aiding data and algorithms transformation.
Why Implementing Privacy-Enhancing Computation Matters
Modern businesses are looking for ways to guarantee consumers that any sensitive information stored with them is safe. We would like to highlight the general reasons to implement privacy-enhancing computation that protects your technological processes.
Why Privacy-Enhancing Computation Is Important For Digital Transformation?
Privacy-enhancing computing is one of the crucial factors for organizations that are reshaping their digital stance. Restructuring repetitive processes and migrating to the cloud are essential to maintain data-driven policies.
In this context, digital transformation requires organizations to constantly challenge current conditions by using policies that bring innovation. Implementation of privacy-enhancing computation (PEC) enables detailed security measures to be put in place, and delivers long-term benefits to organizations and their consumers.
A Range of Privacy-Enhancing Technologies
Privacy enhancing involves technologies are made to secure sensitive data and preserve data privacy, while analytics and sharing processes are performed.
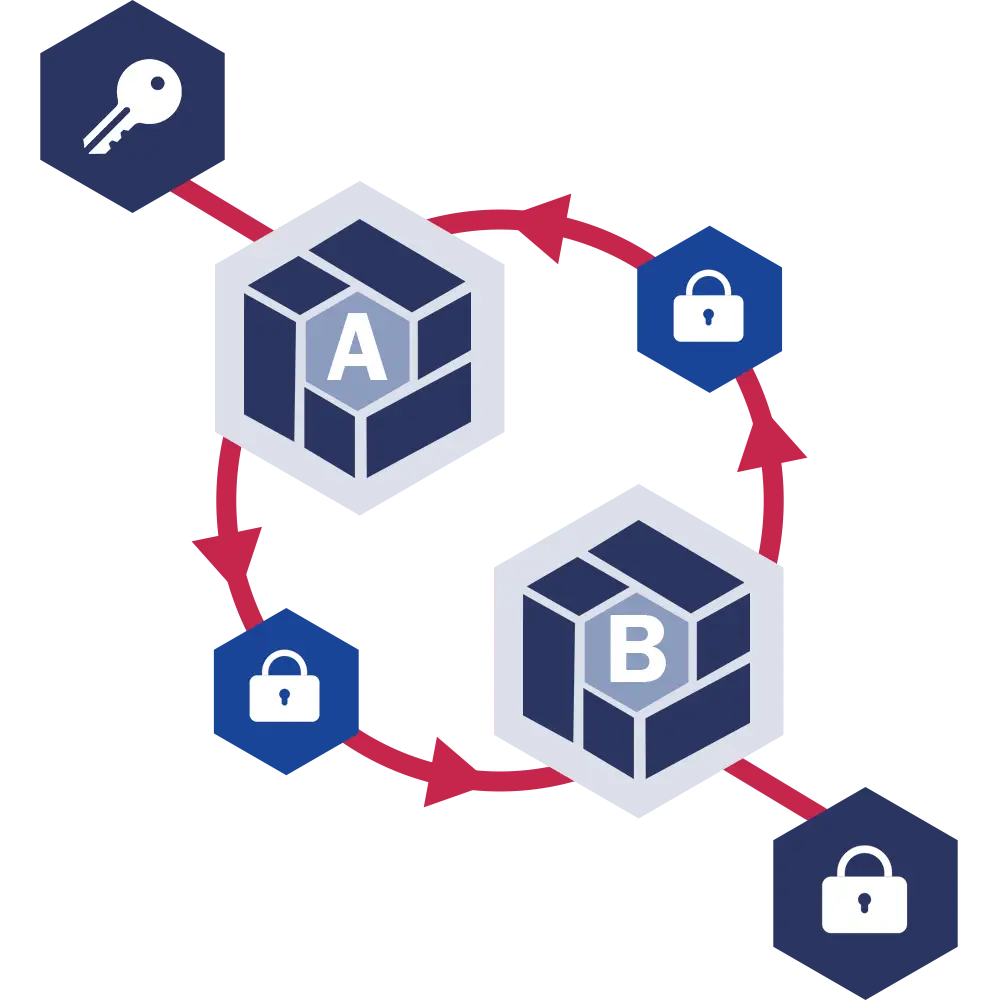
Homomorphic Encryption
Homomorphic encryption is a technology that allows the processing of encrypted data for third-party providers. This is a neat way of protection: the data remains confidential, yet still can be processed. With homomorphic encryption, consumer data used in areas like medical, and banking can be processed by a general index, without requiring private information.
Multi-Party Computation
Secure Multi-Party Computation (SMC) allows multiple parties to analyze various data together without revealing them individually. This means people can analyze consumer data without compromizing privacy. With multi-party computation, different parties have joint computational processes, but nobody can detect or track the input of any other party.

Trusted Execution Environments
A trusted execution environment (TEE) is a privacy preserving environment for the main device. It provides a high level of protection separately from the operating system. TEE covers trusting your device, allowing or forbidding access to your location, photo gallery, and other data for third parties. Asking for a password, authentication code, email or phone verification can also be a part TEE data privacy.

Personal Data Stores
A personal data store (PDS) brings the ability to upload, share, change, or delete this data by the data owner. This type of stores has a range of benefits for a business like:
- collecting and keeping data more effectively
- fewer legal risks of announcing private data without permission
- an ability to easily update data
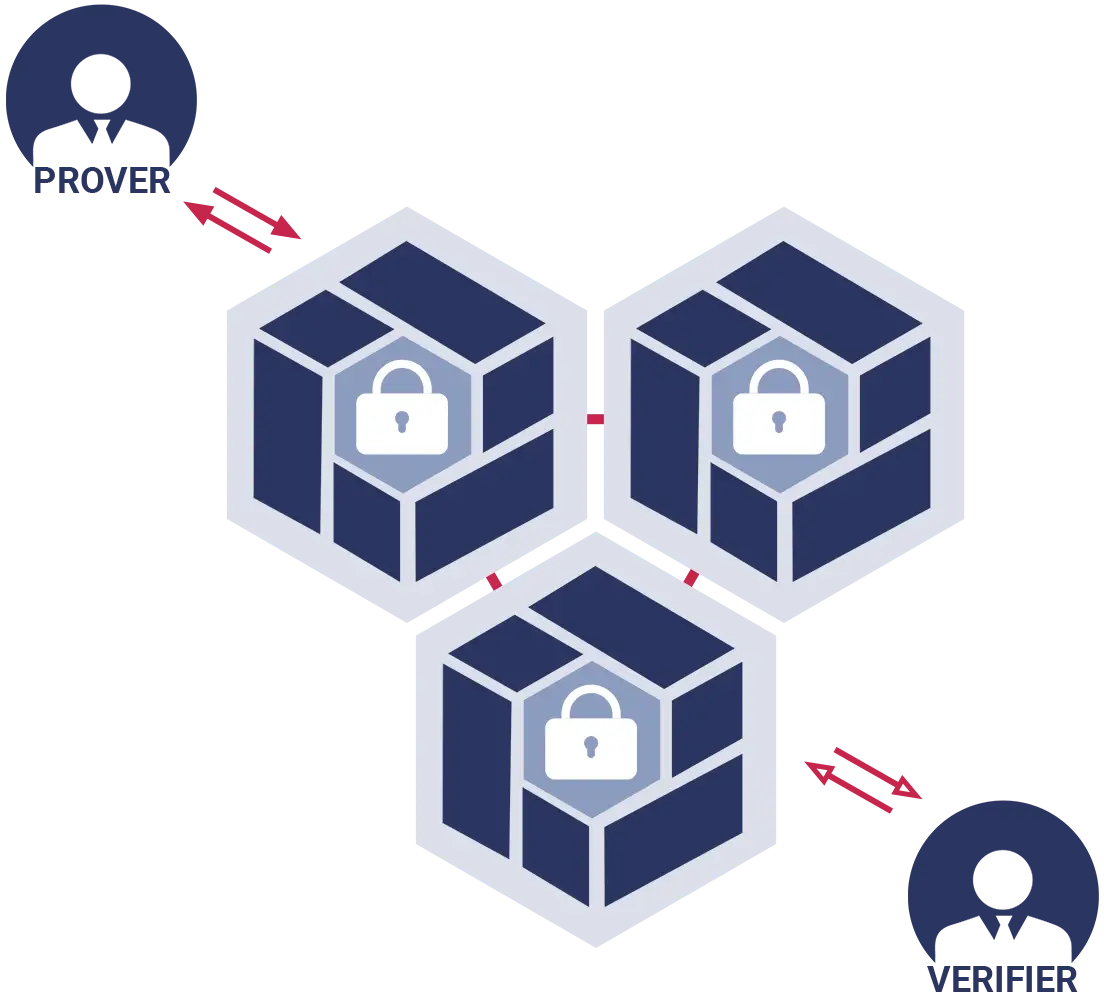
Zero-Knowledge Proofs
Zero-Knowledge Protocol or Zero-Knowledge Password Proof, (ZKP) covers authentications where no passwords are exchanged. With this technology, the verification of data happens without actually revealing any of that data.
Differential Privacy
Differential Privacy algorithms allow information about datasets to be shared without revealing the identities of each participant. The system analyses data and generates statistics while masking individual data. Differential Privacy ensures the security of private data and individual-level information.
PEC Applications: How It Works
Leveraging datasets while maintaining full security unlocks many uses and functions to protect users` private data. Some of the examples are:
PEC's Industries of Use
Privacy-enhancing computation makes it much easier and reliable for any company to keep their data secure. he use of these technologies is broad and can be applied in industries such as:

Business
Most business companies are repeatedly dealing with huge amounts of valuable data – internal as well as customers`. PETs are crucial for adopting by companies that process customers` private data, as their name and reliability depend on it.

Finances
Financial facilities take responsibility for keeping the data confidential and protect it from leaking. As customers make payments using their account number, banks have to eliminate the possibility of private data being accessed by third parties.

Healthcare
In the latest years, the healthcare industry has been implementing electronic health records systems to save and track each patient's data. Privacy-enhancing computation technologies ensure that specific patients` data will be kept protected from cyber threats.
Applications
Web and mobile applications are usually sustained by third-party providers. They cover changes, updates, and testing. PECs help to limit access to user data without interfering with the app's internal processes.
Softwarium's Approach to Data Security
Ready to discuss the benefits of privacy-enhancing technologies for your business industry? Get in touch with our team!